In India, 63 million Micro, Small, and Medium Enterprises (MSMEs) contribute employment of 164 million, 30% of GDP, and around 40-50% exports. However, according to global reports, 43% of cyberattacks target small businesses, and one in two small and medium enterprises (SMEs) has a chance of a cyber breach. Without cyber security protection, these businesses could hamper the country’s economy, as they contribute significantly to the economy.
According to the latest research conducted on MSMEs in India, where 82 top management of these organizations shared their valuable inputs, Figure 1 shows an overview of the cybersecurity posture of these companies. More than 51% of these companies responded they have some kind of cybersecurity control in place. Few of these MSMEs had adopted some kind of standard or framework, such as ISO 27001 (more than 21%) and NIST CSF (around 6%). Around 63% of these organizations do not have any cybersecurity standard or framework adopted. Among those who had responded with some kind of cybersecurity adoption in place, around 29% of those are not having any security policies, guidelines, and guidelines. Closed-Circuit Television (CCTV) (around 17%), security guards (more than 11%), and fire suppression (around 11%) were mostly popular as physical controls among MSMEs. Also, antivirus software (around 30%), firewalls (more than 20%), and authentication solutions (around 14%) were the most popular technical controls for MSMEs.
Figure 1: Overview of MSME’s Cybersecurity Posture
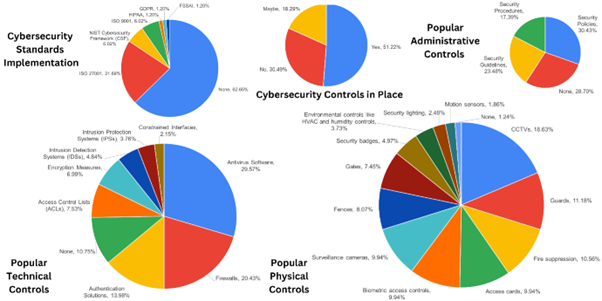
Figure 2 shows the various gaps and problems faced by MSMEs in India. Human beings are always considered the weakest link causing successful cyberattacks. Hence, cybersecurity awareness training plays an important role in strengthening knowledge about the latest cyber threats within organizations.
More than 40% of MSMEs never conducted any cybersecurity awareness training for their employees, which is the biggest threat helping cybercriminals targeting these companies, as illustrated in the figure. Around 39% of MSMEs are sure they have faced cyberattacks.
Around 55% of the MSMEs that have faced cyberattacks are not even aware of the kind of cyberattack they have faced. Insider threats (12%), malware attacks (10.99%), phishing attacks (7.69%), and ransomware attacks (7.69%) were the top four cyber threats faced by those. When being asked about problems faced during cybersecurity implementation, to summarize, MSMEs believe they have financial difficulty (around 25%), lagging knowledge (more than 19%), a lack of resources (around 18%), and other essential business priorities (more than 19%) when it comes to implementing and maintaining cybersecurity.
Figure 2: Overview of Gaps faced by MSMEs

For any MSMEs below are the top ten areas that should be considered for good cybersecurity posture.
1. Host/Endpoint Security: Host/endpoint security is a critical aspect of cybersecurity that focuses on protecting end-user devices such as desktops, laptops, and mobile devices from malicious activities. Endpoint security, also known as endpoint protection, involves securing endpoints or entry points of end-user devices from being exploited by malicious actors and campaigns. With the rise of remote work and the increasing number of devices connecting to corporate networks, endpoints have become prime targets for cyberattacks. Effective endpoint security helps prevent data breaches, malware, and other cyber threats. Few examples are, use of antivirus and anti-malware, regular update with the latest security patches, and implementing host-based firewalls.
2. Data Security: Data security is the practice of protecting digital information from unauthorized access, corruption, or theft throughout its entire lifecycle. MSMEs must identify and classify sensitive data to understand what needs the highest level of protection.
These organizations need to adopt data encryption, secure data storage, the principle of least privilege, access monitoring, and strong authentication.
3. Human Security: The human security layer is a critical aspect of an organization’s overall cybersecurity strategy. It focuses on the actions, behaviours, and decisions made by individuals within the organization, including employees, contractors, and any other personnel who interact with the organization’s systems and data. Security Awareness Training, Phishing Simulations, Access Management, Incident Reporting Culture, and Behavioural Monitoring are a few key factors to be considered.
4. Network Security: Network security is crucial for protecting an organization’s data and infrastructure from unauthorized access, cyberattacks, and other security threats. Network firewalls, intrusion detection and prevention systems (IDPS), virtual private networks (VPNs), and network segmentation are a minimum set of recommended controls to contribute to network security.
5. Application Security: While developing any software, organizations should adhere to security coding best practices such as the Open Web Application Security Project (OWASP). Apart from that, the infrastructure security of the hosting environment is a must.
6. Physical Perimeter Security: Physical perimeter security is crucial for protecting an organization’s facilities and assets. Controls like physical barriers, surveillance systems, intrusion detection systems, lighting, and even security guards should be placed to protect the organization’s assets against any possible threats.
7. Critical Asset Security: Each organization should identify critical assets for their business and must adhere to security best practices safeguarding those against potential cyber threats.
8. Specific Compliance Fulfilment: Security compliance is crucial for organizations to protect their assets and meet regulatory requirements.
It is important to identify the specific regulations and standards relevant to the organization’s segment, such as SEBI, HIPAA, etc.
9. Adhering Requirement of Digital Data Privacy Law: Digital data privacy laws are crucial for organizations to ensure the protection of personal data and maintain trust with customers. Depending on the location or citizenship of the employees or customers, different laws are applicable. For example, General Data Protection Regulation (GDPR) of Europe, California Consumer Privacy Act (CCPA), India’s Digital Personal Data Protection Act 2023, etc.
10. Governance of Overall Security: Security governance is essential for organizations to manage and mitigate cybersecurity risks effectively. It involves a set of processes, practices, and policies that ensure the security of information systems and compliance with regulatory requirements. As cybersecurity is a niche domain, top management of organizations should adopt existing cybersecurity standards or frameworks, such as ISO 27001, NIST CSF, or even the BDSLCCI framework, which provides tailored cybersecurity controls depending on the MSME’s business domain.
References:
[1] Pawar, Shekhar, and Dr. Hemant Palivela. “LCCI: A Framework for Least Cybersecurity Controls to Be Implemented for Small and Medium Enterprises (SMEs).” International Journal of Information Management Data Insights, vol. 2, no. 1, Apr. 2022, p. 100080, https://doi.org/10.1016/j.jjimei.2022.100080.
[2] Pawar, S.A. and Palivela, H. (2023), “Importance of Least Cybersecurity Controls for Small and Medium Enterprises (SMEs) for Better Global Digitalised Economy”, Tyagi, P., Grima, S., Sood, K., Balamurugan, B., Özen, E. and Eleftherios, T. (Ed.) Smart Analytics, Artificial Intelligence and Sustainable Performance Management in a Global Digitalised Economy (Contemporary Studies in Economic and Financial Analysis, Vol. 110B), Emerald Publishing Limited, Leeds, pp. 21-53. https://doi.org/10.1108/S1569-37592023000110B002.
[3] Pawar, Shekhar, and Poonam Pawar. “BDSLCCI.” Notionpress.com, 27 July 2023, notionpress.com/read/bdslcci. Revised Edition March 2024.
